



PC Survival and Maintenance
T.O.M.S.
Introduction
This article is addressed primarily at the many of you out there who are presently running a much-loved but aging RiscPC or even earlier ARM-powered machine. You are considering replacing it but, for a variety of reasons (which need not concern us), you've decided not to get an Iyonix or A9Home.
As an alternative, you are actively considering the emulated solution, VirtualRPC, and in principle are reasonably happy about that. But at the same time you are very nervous about the idea of necessarily superimposing VirtualRPC on a host PC, perhaps because of your unfamiliarity with the Windows operating system and especially the numerous horror stories routinely put about by a very vocal group of people in the mags and on forums.
(Just as this article was being started, the good news came in that a beta version of VirtualRPC for Mac OS had been released. This may change the whole picture for you but, for the moment, we'll stick to discussing the perceived problems with PCs and Windows.) So before you can make up your minds whether to proceed with VirtualRPC or not, an important question which must be answered is just how valid are these horror stories?
Are they all absolutely true; or is there only a little truth in them; or were they true at one time but no longer apply; or are they misconceptions; or are they even misrepresentations? Or all of the above?! You can be sure that, if you were to ask 100 people, you could get 101 different replies...
But as it happens, the four of us currently at T.O.M.S. take a unanimous standpoint on this touchy topic, which is that while some of the above may apply, at least to some extent, every horror story badly needs to be put into a proper perspective.
When that is done, the overall picture changes very markedly and greatly for the better. So what we aim to do in this series of articles is first to look at some of the implications of running RISC OS under VirtualRPC on a 'host' PC which, in turn, is running a reasonably up-to-date version of the Windows operating system such as Windows XP.
Secondly, we'll look at the various horror stories as individual elements and try to put each one into a proper and much more realistic context.
New to Windows?
Recently, in an extensive thread within Archive-on-Line, a contributor posed a series of thoughtful and valid queries which we believe very neatly encapsulates what seems to be bothering a lot of potential VirtualRPC buyers, so we'll repeat them here part-verbatim:
... Assume that I were to buy a system which had been set up so as to boot up directly into VirtualRPC, and was arranged to 'hide' Windows as such. i.e. a result intended to be indistinguishable from a 'native' system for RISC OS...
How often would I find that Windows would intrude into using the result? Thus requiring some dealings with, awareness of, or knowledge of, Windows.
The context would be to buy and use a machine on a daily basis for, say, five years. My point being that if I wish to work without having to deal with, or learn anything about, Windows, and do so for some years using the system, would this be feasible?
If not, then my view is that it is potentially evading the real-world context to treat the native and emulated systems as being 'like for like', without taking this into account in some way.
Very well put and, in a follow-up dialogue with this contributor, he wrote to us:
... I feel that what would really be needed would be a 'survival and maintenance guide' to what Windows information and actions would be required by a VirtualRPC user to ensure they were OK. But I have no idea what that would entail.
As a straightforward 'customer requirement' which we believe probably applies equally to many of you out there we don't think that can be better expressed. So let's see if we can satisfy this clear need.
RISC OS in isolation on a PC?
In principle, it would indeed be possible to configure a PC so that, at initial power-up, VirtualRPC was loaded and the RISC OS desktop as we know and love it would appear (at the very least in a window, but a single mouse click or pressing <Alt-Enter> would then put it into full-screen mode).
Similarly, at the end of the session, pressing and holding the PC power button for about 3 secs would switch off the machine. Seemingly, so far so good.
And to answer the query about whether the underlying Windows would "intrude" into using RISC OS under VirtualRPC, Windows as an operating system will not in itself intrude.
However, we do need to be aware of what other (Windows) application software might be running in the background, i.e. multitasking, and which might intrude upon RISC OS. Such a clash may simply result in VirtualRPC dropping from full-screen mode into a window in which case a single mouse click or pressing <Alt-Enter> would return it to full-screen. A minor inconvenience perhaps?
But conceivably, it could adversely affect an application running under RISC OS and, in the Archive-on-Line thread, there was a sad tale of Ancestor+ being corrupted by the Windows anti-virus application AVG Free. As the latter is an acclaimed and highly recommended safety device, this clash is unfortunate. But there's a quick fix as it's an easy task to configure AVG Free so that it doesn't interfere with RISC OS after all (discussed later).
After getting on for four years experience of using VirtualRPC, this is the only intrusion that we know of. That doesn't mean to say there are no others, but one would hope they can also be dealt with in a similar, unobtrusive manner.
However, this is just one example of where you may want to delve into the Windows working environment after all (in the above instance, not the operating system itself, but an application running under it), and which therefore will require at least a modicum of familiarity with the Windows filer etc. But don't think that's in any way a significant problem. Depending on your viewpoint (Is my glass half-full or half-empty?) it may appear to be easy or complicated. Yet when you actually come to do it, it's really very straightforward and largely intuitive. If you already know RISC OS, you're very unlikely to have any problems with this modest level of activity under Windows.
Another situation is that, sooner or later, you may wish to improve on the facilities available to you under the default VirtualRPC installation. An example is that if (say) your real RiscPC came with 32MB RAM and 1MB VRAM, maybe you took the lid off, stripped it down, installed more RAM, swapped the VRAM for a 2MB module and put it all back together again. Not an insignificant task for anyone who may not be 'computer savvy'.
With VirtualRPC, it's pre-configured with a minimum of 8MB 'VRAM' anyway, so already there's lots more pretty pixels available to you, provided you have a suitable monitor and change the ConfigurationScreen setting under RISC OS (which you would have to do anyway on an ARM-powered machine).
When it comes to increasing the RAM, there's no new module to buy or dismantling involved; you simply reconfigure VirtualRPC to use more of the PC's installed RAM. But to do that, you need to delve into the VirtualRPC directory via Windows and tweak the numbers accordingly, changing from the default 2Χ16MB settings to a maximum of 256MB RAM.
Be assured this really is a simple task, entirely in software and which can be done in a minute or three (remember, no physical dismantling is involved), but it does require a very basic knowledge of how to find the PC's hard disc drive icon (double-click on My Computer), how to step through the directory structure to get at the 'Model' file within VirtualRPC (just keep double-clicking), how to change the RAM setting (click in the relevant line and type in the new number) and how to re-save the Model file (press <Ctrl-S>). Of course, all this is fully covered in the VirtualRPC user-guide.
A third and more general reason for wishing to delve into the Windows environment is in order to use its inbuilt features which, for whatever reason, you may well find suit you better than those within RISC OS and its available application software.
A very common instance of this is that none of the current crop of RISC OS browsers may allow you to access 'difficult' sites such as your e-bankers.
A quick and very easy solution is to nip into Windows, fire up any one of the available browsers (Internet Explorer being an integral part of the repertoire of Windows application software), access the site(s) and get the information you want. If you wish, you can even save the pages in HTML format, move them back via VirtualRPC and then access them using any RISC OS browser.
This is a typical example of the 'best of both worlds' scenario which the combination of splendid RISC OS and Windows applications working with each other can give you. On the other hand, it will necessarily require very basic familiarity with how to drive Windows and its range of goodies.
But to reiterate, we very firmly believe that this is not difficult to grasp for anyone (regardless of age!) who is already RISC OS-savvy, given a modicum of 'getting-to-know-you' plus of course the will to do so, which not everyone has by default.
Survival & security techniques
Mention of the anti-virus program in the previous section naturally leads us to the most worrisome group of horror stories, and that is the collection of viruses, spyware, rootkits and like infections which potentially can make a complete mess of one's PC. If the stories are to be believed, all the myriad nasties out there will get into your machine, will destroy its integrity and your privacy and even slow the PC down to a crawl.
Is any of this true? It possibly is to a small extent; we simply have no firm evidence to gainsay it. But what we can say with total confidence (based on the average 15 or so years that each of us have been using PCs, in different environments including business and in the home) is that we have never knowingly suffered ill-effects from any viral attack, nor any loss of security or privacy through spyware or rootkits etc, nor even the inconvenience of seeing pop-up ads.
So maybe the reported nasties simply do not exist, in their entirety and/or we must be doing something right in inoculating ourselves against them. We simply don't know which, but it would be very unwise not to assume it's the latter. So we do take all sensible precautions but, at the same time, we never let them intrude into our day-to-day use of the computers, including VirtualRPC.
These precautions take two forms: firstly, common sense usage of our PCs and, secondly, the installation and use of suitable anti-nasty software.
The common sense precautions are very simple and wholly non-intrusive:
- We never, ever open an email attachment unless we're absolutely sure it's from a known 'friendly'. Reportedly (although hearsay), 90% or more of viruses reside within email attachments.
- We avoid dodgy websites. Although again purely hearsay, it's the so-called 'adult' sites which contain most of the remaining 10% or so viruses.
- If we intentionally install and use non-commercial software for Windows, we make efforts to get it from reliable sources such as magazine cover discs (e.g. PC Advisor) or the better-known freebie-software providers, first checking all products are guaranteed virus- and spyware-free. We suggest www.filehippo.com which has an excellent selection in many useful categories.
As for the choice of protection software, you need to be a little bit canny. For example, many broadband modem/routers and Windows (XP with Service Pack 2 or later and, presumably, Vista) has a built-in 'firewall', but you do need to set it to be active it will clearly warn you if it isn't.
What a firewall actually does isn't made terribly clear but, for our purposes, it's entirely unobtrusive, doesn't need regular scanning and, on the face of it, remains invisible until it sees something it isn't quite sure of. So it will put up a warning message if, say, you try to install some software it doesn't recognise, but doesn't stop you proceeding if you opt to do so.
When it comes to anti-virus software, it's quite likely that a third-party, commercial offering will be pre-installed in a new PC. But beware of that; it will probably be a loss-leader, its virus 'signatures' will almost certainly already be out of date when you get the PC and, even if it comes with (say) a 60-day 'free update service', after that it becomes progressively expensive to maintain.
And according to objective testing in magazines, etc, they don't appear to be particularly efficient in finding viruses anyway. So all in all, if a new PC comes with one of these freebies, we suggest you uninstall it and, instead, go for something which comes out much higher in the performance listings.
So which one is that? The final choice is of course the user's but, time and again, AVG Free (presently at v7.5) comes very high up the charts and is strongly recommended by many users, including ourselves, for the excellence of its anti-viral protection and sheer ease of use. Although a 'lite' version, with a price to match (FOC...), its features include everything we need and, to reiterate, it has never knowingly let anything through.
Configuration and use will be discussed in Part 2. If it sees a nasty, a warning message is generated, allowing the user to either heal the virus on the spot, or move it to a safe place (the 'Virus Vault').
To protect against spyware, Microsoft have now released a full version of their own solution, called Windows Defender (currently at v1.1). This is so unobtrusive that we've never seen any warning message! But nor has it ever reported any spyware during full scans, so is it effective? In principle, there's nothing to stop the user adding to the level of protection by installing and running two or even more like applications, on the basis that one may intercept something another has missed.
To that end we run Ashampoo AntiSpyware (currently at v1.61), in parallel with Defender, as it also has a 'rootkit' detector which does very occasionally pick up and delete some reported nasty. Although this is a commercial solution ($29.99, available direct from www.ashampoo.com), we found it on a magazine disc, with a free registration code.
Finally, the question of privacy. In order to greatly speed up access to previously-visited websites, for example, Windows browsers do tend to retain a detailed record of your usage, but of course this can affect your confidentiality which, hopefully, the firewall(s) will protect against outside access.
But if you simply delete the records (cookies etc) from hard disc, this affects only the disc catalogue not the records themselves so a determined snooper might still be able to access them.
A far more rigorous approach is occasionally to run an application which takes the deleted files (including the Recycle Bin contents if configured to do so) and overwrites them with 'scribble', repeatedly, rendering them wholly unreadable. Typically you may be able to select a 3-pass overwrite (for speed), 7-pass (quoted as meeting US National Security Agency standards) or yet more (even safer but relatively slow). For this purpose, we use CCleaner (Crap Cleaner!), currently at v1.40 and which, once again, is free, entirely unobtrusive and simple to use (Fig 1).
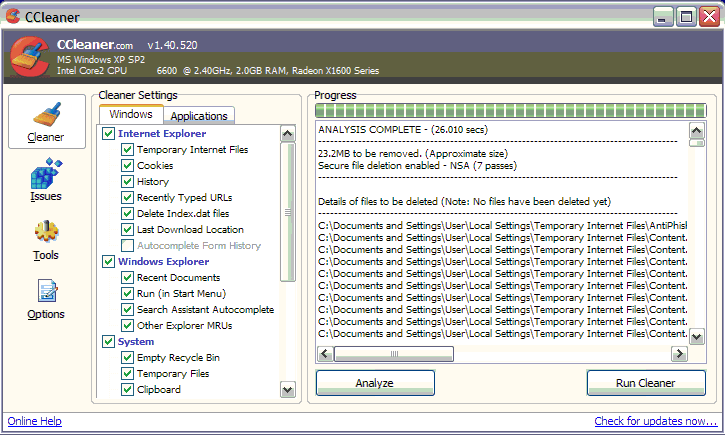
Fig1. CCleaner
Installing Windows applications
We've glibly spoken about using various Windows application software titles, but how easy are they to install and configure? The brief answer is "Simple".
However you obtain the titles maybe on CD or perhaps downloaded from www.filehippo.com you'll be presented with the application's installer (named <title>.exe), when it is simply a case of double-clicking on the icon which will launch the application's 'wizard'.
This will take you through the install procedures and may present you with very simple set-up options, or may just allow you to accept all the default settings, doing virtually all the work for you; it's normally very friendly.
So a knowledge of Windows procedures is not really necessary for these operations, but it may help.
Coming in Part 2
In the next part we are going to cover routine machine servicing, installing updates to Windows, anti-virus products and more.
T.O.M.S.